AWS Config provides a detailed view of the configuration of AWS resources in your AWS account and is a powerful tool for security and governance.
AWS Config can record and track changes to the configuration of many types of resources in AWS. Config Rules can be created to define your ideal configuration settings and then run to evaluate the configuration of your AWS resources. AWS Config provides predefined rules, called managed rules, as well as allows you to create custom rules using AWS Lambda to define custom logic that AWS Config doesn’t yet record. Currently, there are over 200 predefined managed rules in AWS Config.
If resources drift from these settings, AWS Config can notify you, for example, if your Amazon S3 bucket doesn’t have versioning enabled, or if EC2 instances have a public IP association which might not always be desirable from a security or compliance standpoint.
These rule options can be incorporated into a broader compliance policy. A typical company’s policy might state that:
- All data must be encrypted at rest.
- The AWS IAM password policy must meet the corporate standard.
- Resources must be billed to the correct cost center.
- Want to know who owns a resource in case there is an issue or question about the resource.
- Want to identify whether a resource is a part of Dev, QA, Production, or staging so that we can apply the correct SLAs and make sure the appropriate teams have access.
AWS Config is not free and the number of configuration items recorded (configs are stored in S3), and each active rule incur charges. The pricing is detailed here and is not too expensive if properly managed. Keep in mind that pricing could add up quickly if there are a lot of monitored resources that change frequently in your AWS environment.
Following are the steps to enable AWS Config and create a managed rule to check if logging is enabled for your S3 buckets.
Step 1: Enable AWS Config.
Click Get Started button for manual setup
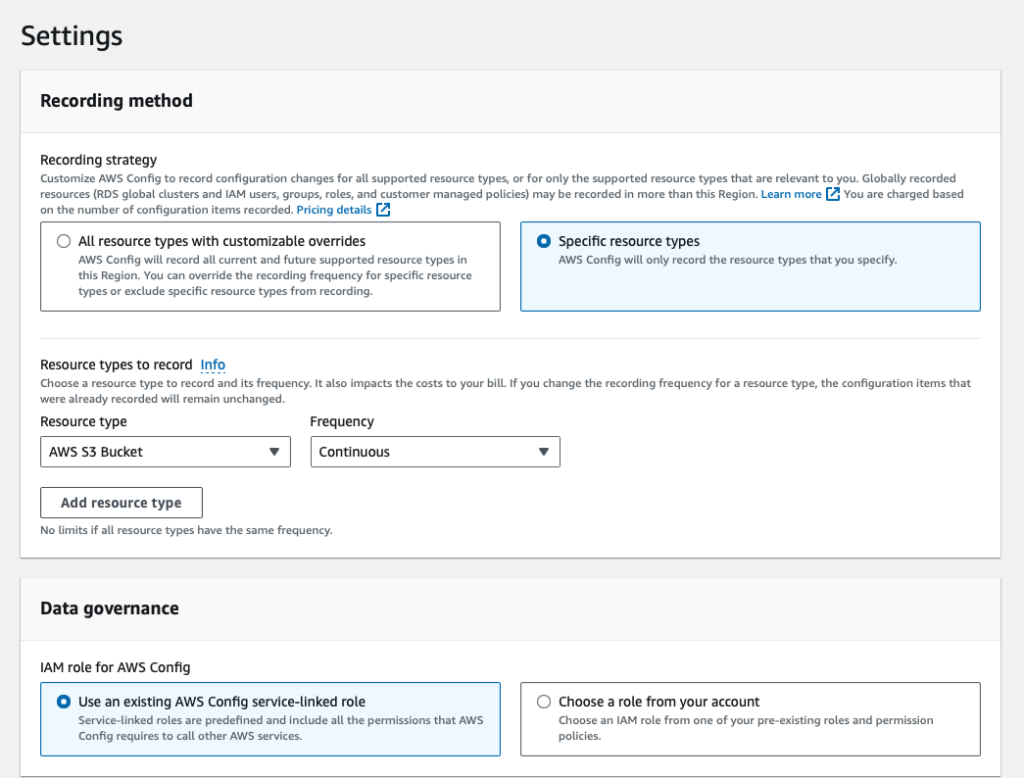
Step 2: Configure Settings
Make the following selections:
Recording Strategy: Specific resource types
Resource type: AWS S3 Bucket
Frequency: Continuous
Data Governance: Use an existing AWS Config service-linked role. I have the following role under IAM: AWSServiceRoleForConfig
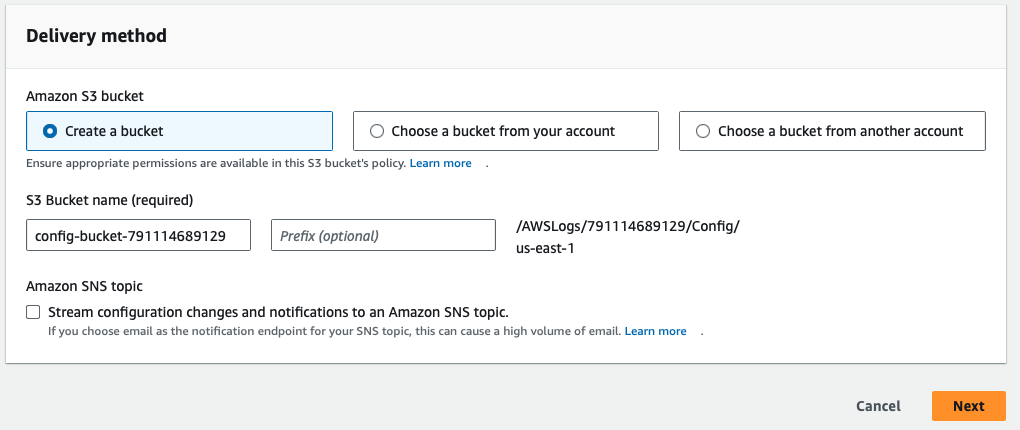
Delivery Method: Create a bucket (It will auto-populate the name)
Click Next
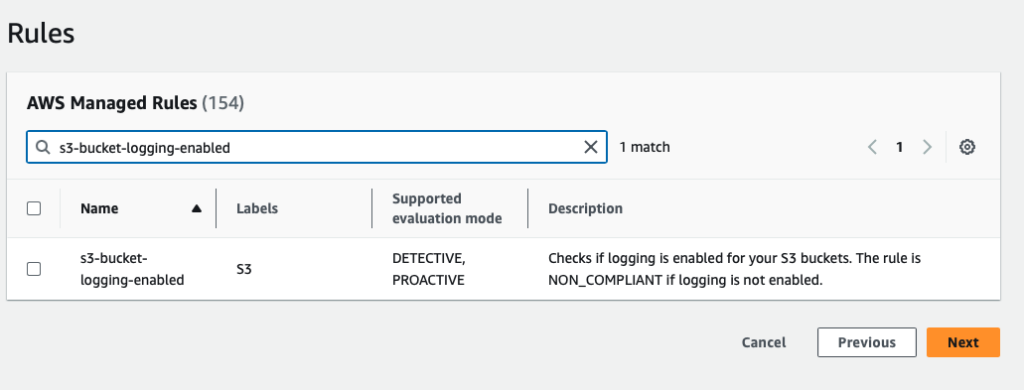
Step 3: Define a rule
Select AWS Managed Rules: s3-bucket-logging-enabled
Click Next
Step 4: Review the resource type and rule
Review and click Confirm
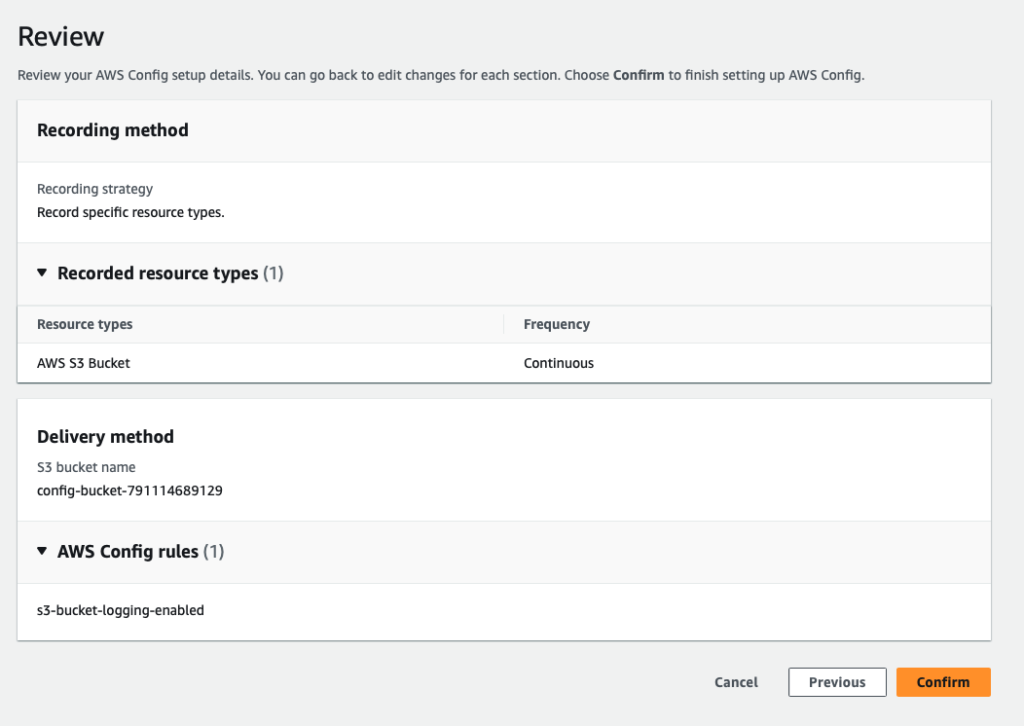
The above steps will set up your recorder and create a rule. You can also verify the recorder via the CLI as follows:
aws configservice describe-configuration-recorders
{
"ConfigurationRecorders": [
{
"name": "default",
"roleARN": "arn:aws:iam::791114689129:role/aws-service-role/config.amazonaws.com/AWSServiceRoleForConfig",
"recordingGroup": {
"allSupported": false,
"includeGlobalResourceTypes": false,
"resourceTypes": [
"AWS::S3::Bucket"
],
"exclusionByResourceTypes": {
"resourceTypes": []
},
"recordingStrategy": {
"useOnly": "INCLUSION_BY_RESOURCE_TYPES"
}
},
"recordingMode": {
"recordingFrequency": "CONTINUOUS",
"recordingModeOverrides": []
}
}
]
}Step 5: Review S3 buckets
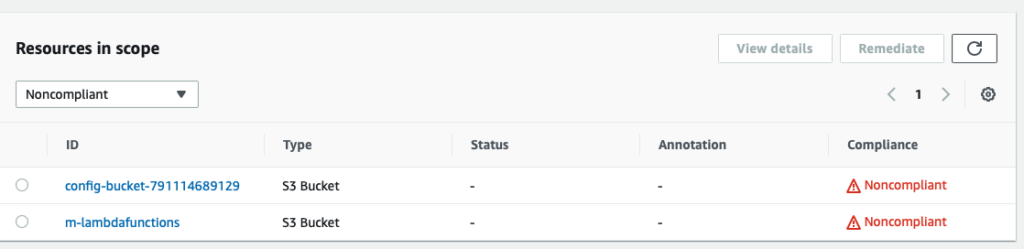
I already had a m-lambdafunctions S3 bucket to store Lambda functions. You will notice a new S3 bucket was created to store configurations.
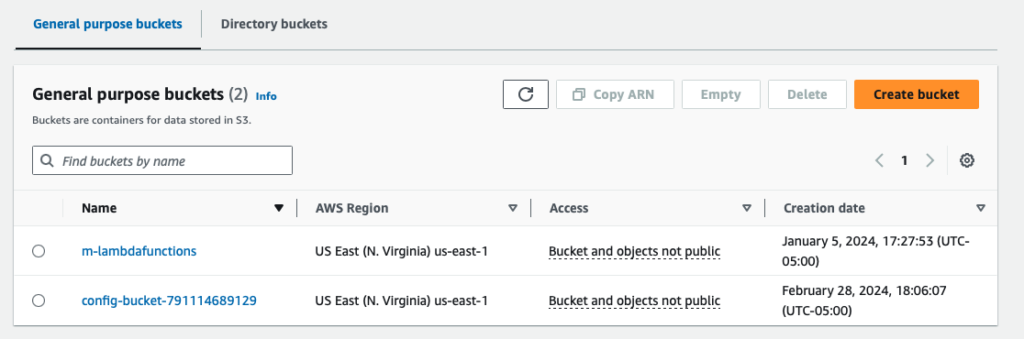
Both buckets had server side logging disabled
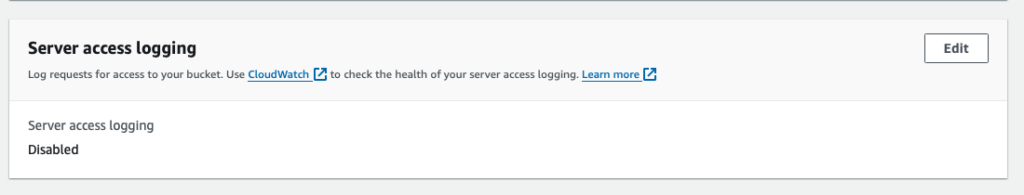
Step 6: Validate the rule
Click the Rules tab on the left console. Since we specified Frequency as Continuous during the setup above, the rule will fire immediately and provide compliance results
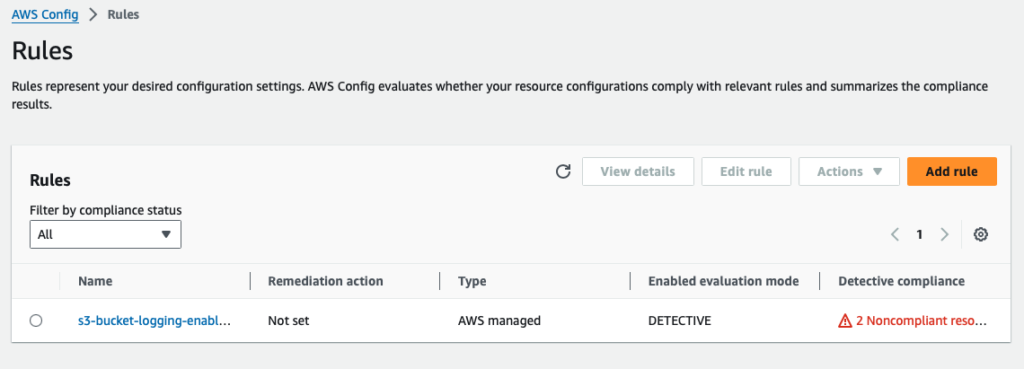
The two S3 buckets do not have server side logging enabled.
Step 7: Clean up resources
Clean up resources to avoid any unnecessary charges. I deleted the recorder via the AWS CLI as follows
aws configservice delete-configuration-recorder --configuration-recorder-name defaultPlease delete the Config S3 bucket manually.
References:
- https://docs.aws.amazon.com/config/latest/developerguide/s3-bucket-server-side-encryption-enabled.html
- https://docs.aws.amazon.com/config/latest/developerguide/dynamodb-table-encryption-enabled.html
- https://docs.aws.amazon.com/config/latest/developerguide/evaluate-config_use-managed-rules.html
- https://aws.amazon.com/config/pricing/
- https://github.com/awslabs/aws-config-engine-for-compliance-as-code
- https://docs.aws.amazon.com/config/latest/developerguide/evaluate-config_develop-rules_nodejs.html
- https://docs.aws.amazon.com/config/latest/developerguide/evaluate-config_develop-rules_getting-started.html#gs-create-lambda-function-for-custom-config-rule
- https://aws.amazon.com/blogs/mt/deploying-custom-aws-config-rules-in-an-aws-organization-environment/
